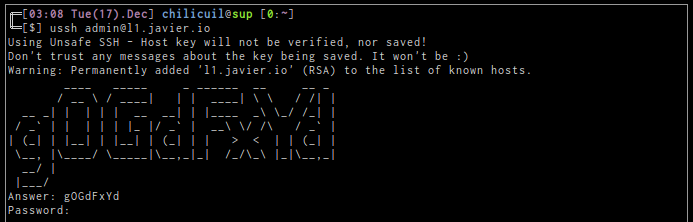
ssh captcha
17 Dec 2013
Some days ago while I was reviewing some data I noticed a spammer in one of my remote machines. Since I was mostly using the box for running experiments I decided to rebuild it. Upon completion, I decided to improve my default ssh settings. I just liked too much to use a single password for all my ssh needs 😞
I know some ways to improve security, I could change the password to a really difficult one, change the default port, filter by ip, by tries (fail2ban), disable completely password login and allow only key based logins, etc.
At the end however I decided to just add a captcha protection, why?, most of the ssh attacks are automatized, people run scripts who tests thousand of passwords and run certain commands on success, these scritps won’t be able to recognized the slighly modification in the login process (they’re really dumb). In the other hand, I don’t need over complicated solutions, or more systems to administer. Ssh key based login is great but sometimes I just need access from third party machines.
Lastly some other popular solutions have come up but for one or other reason I couldn’t feel comfortable with them:
- google authenticator (my cellphone is most of the time lost, turn off or without battery, do I live under a rock?, not at all!, but I don’t get the always online hype.)
- barada (see above reason)
- otpw (printing and carrying passwords with me?, you must be kidding)
- otp (I may try this one)
- github auth (unrelated but it’s a nice way to do pair programming fast)
- authy (people seems to really like cellphones)
- any other method who involves ForceCommand
Installation
$ sudo add-apt-repository ppa:minos-archive/main $ sudo apt-get update && sudo apt-get install libpam-captcha
Be aware than the previous steps will only work in supported Ubuntu LTS versions.
Extra
Sentry
If additional security is desired consider using sentry over fail2ban, denyhosts, sshblacklist, etc, really.
$ wget http://www.tnpi.net/internet/sentry.pl
$ sudo perl sentry.pl
$ echo "sshd : /var/db/sentry/hosts.deny : deny" > hosts
$ echo "sshd : ALL : spawn /var/db/sentry/sentry.pl -c --ip=%a : allowsendmail: all" >> hosts
$ cat hosts /etc/hosts.allow > hosts.allow
$ sudo mv hosts.allow /etc/ && rm hosts
Fail2ban
The next fail2ban regex will match the ssh captcha generated messages
#/etc/fail2ban/filter.d/sshd.conf
^%(__prefix_line)s(?:error: PAM: )?Permission denied for .* from <HOST>$
Thanks Jordan! 😊